This article is a quick one about my annual tradition – participating in Hacktoberfest, the “month-long celebration of open-source projects, their maintainers, and the entire community of contributors.”
It’s a cheesy way to call an October-long event, where a private company tracks qualifying open-source contributions from everyone who signs up (and gives them their contact details for marketing purposes), but I like to think the event is net positive, and participating has become a tradition for me. :)
So just like the last few years, I reserved a couple of my October evenings for some open-source contributions.
Background
Finding the time for some non-work-related coding is hard nowadays, and really, finding some time for ANY coding, even at work, can be challenging. But Hacktoberfest is a great excuse to abandon the family for a few nights and instead of dabble into some interesting open-source projects :)
I mean – my GitHub wall looks like this, so I guess it’s pretty obvious open-source is not what I usually do:
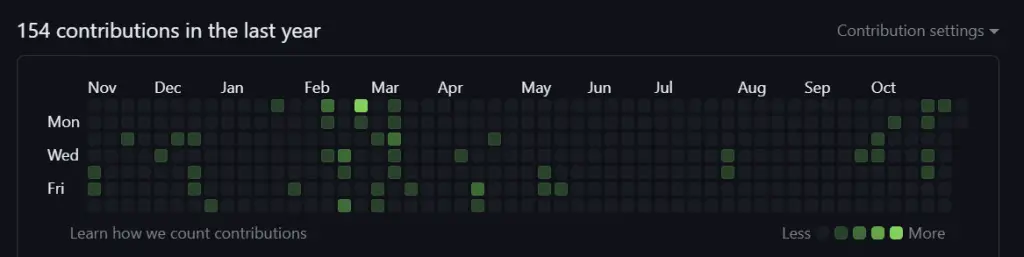
That’s even more of a reason to participate at least once per year, I guess.
No t-shirt this year
Maybe it’s a sign of the times, but gone are the t-shirts and stickers of yesteryear – now all of the reward swag is digital.
And what swag it is!
…That’s actually a real question, because I have no idea what “Holopins” are and what I can do with their badges. On second thought, I guess I don’t need to find out either…
But hey – while the T-shirt was nice and I appreciated the stickers, too, the point of the month-long hack is to contribute to the open source ecosystem and make a positive impact, not to receive swag. The material and handling costs must’ve been significant for the organizer, which puts additional pressure on the commercialization of the sponsors and handling of the participant contact information. Hauling packages around the world causes CO2 emissions, too. And of course there are the issues with customs – something I’ve run into in the past, too. Dropping the swag unfortunately makes perfect sense for the organizers.
And as a result, I suspect the number of participants was lower this year than it’s been for the past few years – people love free stuff, and getting a free t-shirt was a sweet perk. Sweet enough I would’ve happily paid a few euros to “unlock” it after qualifying otherwise, should that have been an option… :)
Instead of what this is:
Anyway. What did I actually manage to do this year? :)
My contributions during Hacktoberfest 2023
Let’s take a quick look – like last year, I wanted to contribute to something I actually use, and where I can be of concrete help. Last year, I had a lot more fun with the actual “work” than the years before, as I collaborated with the maintainers instead of just blindly submitting something that might or might not address an issue already out there on GitHub. Which arguably should be what everyone should’ve been doing all along…
So these are the things I came up with:
| Name | What | Where |
|---|---|---|
| Implement adding labels to terms in SharePoint term store | Turns out that adding non-default labels to terms in SharePoint term store didn’t work in PnP Framework. This was probably because using CSOM to update labels is confusing to say the least. I figured this out by reading a couple of existing Issues – namely, these 2: – TaxonomyExtensions.ImportTermSet does not use the LCID provided in the input PnP-Sites-Core#662 – [BUG] Import-PnPTaxonomy ignores Lcid powershell#3096 Took a bit of debugging to figure what was the safest way to implement the functionality without changing anything unnecessarily. Backwards compatibility is something I value after working in a corporate setting for some years… 😅 | pnp/pnpframework#934 |
| Fix the following bug: Rename-PnPTenantSite not working as expected in Tenants with vanity url. | Vanity URLs in cloud domains can be incredible – in this particular case, PnP PowerShell was validating the admin center’s URL, and replacing it with what it thought was valid. After a bit of deliberation and some back and forth, the unnecessary bit of validation could simply be removed. | pnp/powershell#3533 |
| Fix the bug where all -UseWebLogin auth requests go to the root site collection and implements an override for site-relative auth URI. | PnP PowerShell’s WebLogin (cookie) authentication was (likely by mistake) always redirecting the authentication request to the root site in SharePoint Online. I have to assume not THAT many users actually use WebLogin anymore (good!), or this would’ve surely been picked up before… It was finally a pretty quick fix. And I added a nice extra switch if the user wants to specify which page on the site to use for authenticating :) | pnp/powershell#3530 |
| Add retry logic to Submit-PnPSearchQuery | This PR adds a retry logic around submitting search queries. Useful for large requests (which need to be paged) as SharePoint Search can occasionally time out or return internal errors seemingly without any actual reason, and a simple retry will fix it. | pnp/powershell#3528 (wasn’t accepted in time, though) |
| Update submitsearchquery docs | Since I was working on the previous issue and playing around with Submit-PnPSearchQuery, I noticed there were a few things I could improve in the documentation. :) | pnp/powershell#3527 |
This year’s Hacktoberfest ended up being super useful for my work, too – I happened to talk with a colleague about a very random-sounding issue they were having while trying to authenticate to SharePoint Online using PowerShell on a pretty restrictive tenant, and the weird error messages they got back. I had just been fiddling with web logins due to one of the Pull Requests, and after debugging the login and the issues for a bit, we figured that we can just use -UseWebLogin and see what happens.
And what did we learn? -UseWebLogin bypasses certain authorization requirements that we had hit earlier, and we could proceed scripting a solution for said customer! This legacy auth feature saved the customer a couple of weeks of (calendar) time and our employer some frustration and money.
How nice is that? 😀
Anyway – with the parting words from DigitalOcean, the company actually hosting and organizing Hacktoberfest annually: See you for 2024 – Keep contributing!

(please do keep contributing, as I probably don’t have the time or remember to…)