This post was most recently updated on October 4th, 2021.
4 min read.A couple of days ago, I got a comment asking how to fix error AADSTS90008 when developing an application using Azure Active Directory
The error in question was this:
AADSTS90008: The user or administrator has not consented to use the application with ID ‘[guid]’. This happened because application is misconfigured: it must require access to Windows Azure Active Directory by specifying at least ‘Sign in and read user profile’ permission.
While the error itself is usually fairly simple, explaining what to do in a comment field turned out to be clumsy – so I decided this solution warrants another blog post (even if just barely)!
What went wrong?
AADSTS90008 can mean a couple of different things. Let’s start from simple to more complicated ones:
- Permissions to sign in has not been requested.
- Permissions to sign in have not been granted.
- Granting the permissions to sign in has failed.
Depending on the reason, the solution is of course different as well. I’m going through some simple steps to fix all of these problems – read on!
Solutions to AADSTS90008
Let’s start from the simple one and continue to the more complicated ones.
Time needed: 30 minutes
A couple of possible ways to fix AADSTS90008
- Add your app registration the permissions to sign in
This might come off as a no-brainer, but trust me, it’s not. You wouldn’t believe how easy it is to forget to request a permission! Always worth it to make sure you actually did have this permission scope defined in the permissions you require for your application.
So, this is how you do that:
1. Navigate to https://aad.portal.azure.com
2. Select “Azure Active Directory”
3. Select “App registrations”
4. Find your application from the list
5. Select Settings -> “Required permissions”
6. Add “Graph API” if it isn’t added already
7. Add “Sign in and read user profile” delegated permission, if it isn’t selected already
8. Click “Save”
The pictures below should help illustrate the steps a bit – below, selecting the “Required permissions”…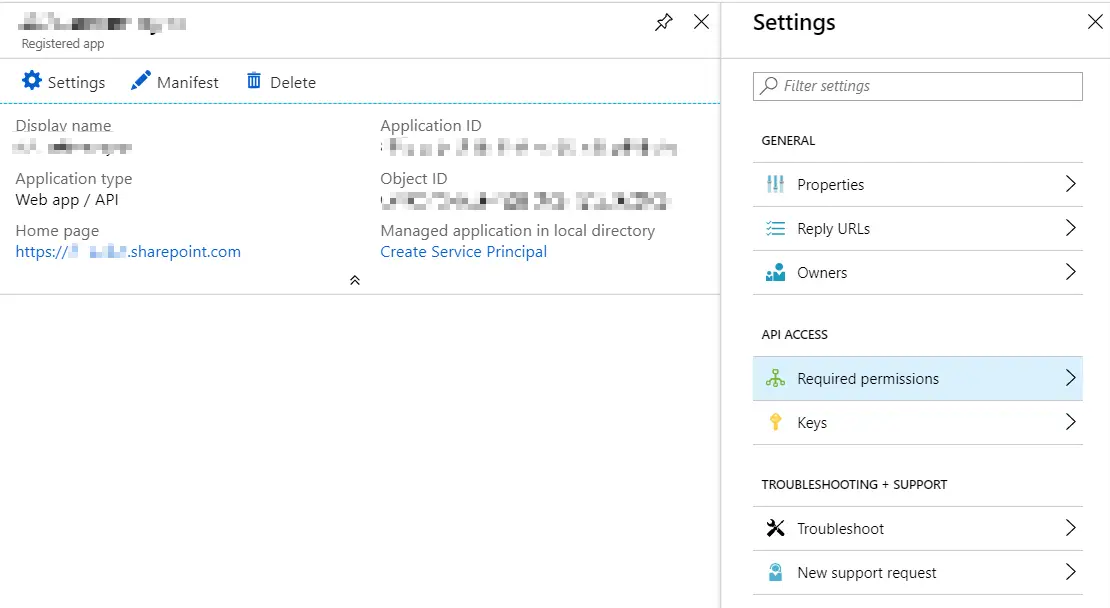
How to edit permission requests for an application registered to Azure Active Directory?
And that will take you to the view where you can actually select and add the required permissions. - How to grant the permissions to sign in for your application?
Okay – so after making sure you have the required permission scope, you still get the same error? No worries, next step is easy.
You’ll need to make sure, that you’ve granted the application access to either your data (which you can do yourself, if the Azure Active Directory’s settings allow that and the application only wants delegated permissions without admin-consent) or to all users (which requires an administrator to grant the permissions).
Navigate to the same page you had navigated in the last step to. Note the “Grant permissions” button in the “Required permissions” view. Click that and verify – and test your app again.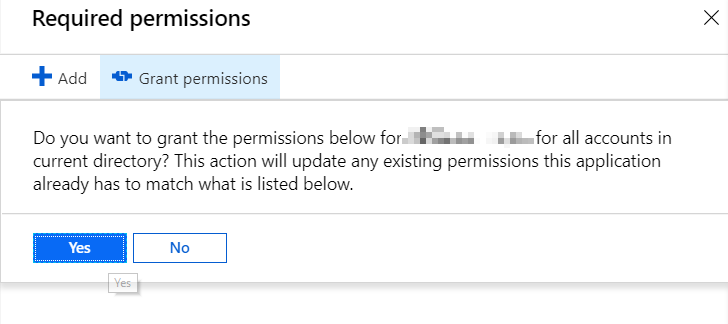
“Grant permissions” in Azure Active Directory application registration will ask for your confirmation, before letting you grant consent for all users.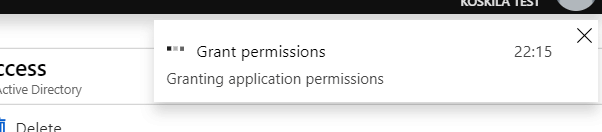
Azure Active Directory is now granting consent to all users…
Be mindful of the next message that pops up – it if looks like the one below, OR if it says “Successfully granted permissions for application [yourapplication] for all users”, you’re good.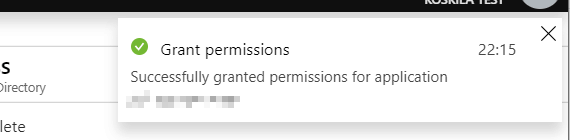
Azure Active Directory has now successfully granted permissions to the application for all users.
It might also say “Successfully granted permissions for application [yourapplication] for your user account”, and look like it was successful. This is an unfortunate user interface design decision in the Azure AD management portal.
In that case, it actually didn’t do much – because the account used wasn’t an administrator with enough permissions to execute the task you tried to execute! You’ll need to give your resident AD admin a firm kick in the butt and make him get you the
global admin or cloud app administrator. That’s who you’ll need in this case. - (OPTIONAL): If granting consent fails, you’ll need to apply some AAD magic to fix it
If you, or your resident administrator friend, run into issues in this step, check out this post to see more options on how to grant the consent for the app.
https://www.koskila.net/how-to-fix-admin-consent-issues-aadsts65001/
At this point you should be good. But if you’re not, there’s still a few configuration steps we can try. - Granting consent/permissions was successful but you still encounther the same issue?
Let’s hope you don’t end up here! There’s probably a lot more that could be wrong, but let’s go through a couple of fixes you can try!
If you’re running ASP.NET in an Azure App Service or you’re running Azure Functions, and you have registered your app for that, you could try this tweak:
1) Navigate to your Azure Application Service or Function App -> Authentication/Authorization -> Authentication Providers -> Azure Active Directory
2) Change the reply url of your application registration to https://[yoursite].azurewebsites.net/.auth/login/aad/callback - One more workaround to try…
Still didn’t work? Change your AAD authentication configuration into Advanced mode, add your ClientId, ClientSecret and IssuerUrl to the configuration.
Issuer Url comes from AAD > App Registrations > Endpoints. Copy Url for FEDERATION METADATA DOCUMENT, paste it in a browser. In the EntityDescriptor tag, there is a property called entityID. Copy that value into the Issuer Url of the WebApp’s Auth config.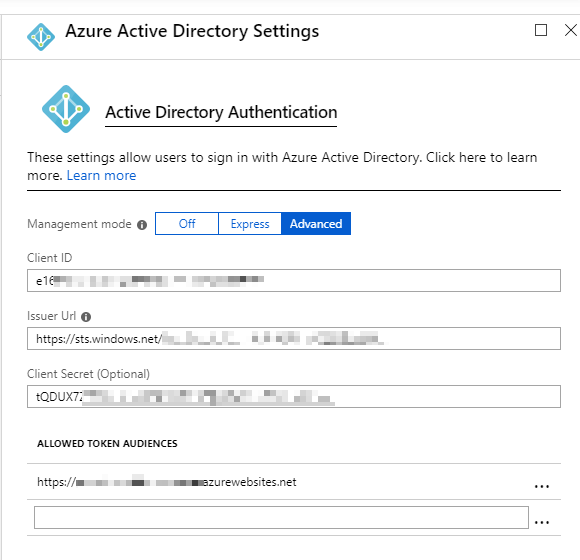
Azure App Service or Function App Authentication settings for Azure Active Directory
Didn’t fix your issue? Did the UI change again and screenshots become outdated?
Let me know in the comments below!
Further reading
- https://social.msdn.microsoft.com/Forums/en-US/00437a0f-3a12-405f-b369-36c00fd51a0f/receiving-a-aadsts90008-error-despite-having-correct-application-permissions?forum=WindowsAzureAD
- https://docs.microsoft.com/en-us/azure/app-service/configure-authentication-provider-aad