This post was most recently updated on August 26th, 2022.
5 min read.Whilst running some SharePoint Online PowerShell commandlets, or connecting to a SharePoint Online site from your app, you get the following (or similar) error about your SharePoint Online credentials being unauthorized for something you should definitely be authorized to do:
Cannot contact web site ‘https://[tenant]-admin.sharepoint.com/’ or the web site does not support SharePoint Online credentials. The response status code is ‘Unauthorized’.
And that’s not all – by digging into the full error message, you find the underlying internal error:
MSDAVEXT_Error=917656; Access+denied.+Before+opening+files+in+this+location%2c+you+must+first+browse+to+the+web+site+and+select+the+option+to+login+automatically.
What awakens my curiosity, is this line:
Access denied. Before opening files in this location, you must first browse to the web site and select the option to login automatically.
However, when you open your browser, you can actually log in without a hitch. If that’s the case, this might be a weird internal error in SharePoint Online. Nothing you can do permissions/configuration-wise, but luckily – there’s a hazy and weird, but simple PowerShell-based fix!
Description of the issue
The whole error might be something like this:
Cannot contact web site 'https://[tenant]-admin.sharepoint.com/' or the web site does not support SharePoint Online credentials. The response status code is 'Unauthorized'. The response headers are 'X-SharePointHealthScore=0, X-MSDAVEXT_Error=917656; Access+denied.+Before+opening+files+in+this+location%2c+you+must+first+browse+to+the+web+site+and+select+the+option+to+login+automatically., SPRequestGuid=, request-id=, MS-CV=[i_don't-even-know], Strict-Transport-Security=max-age=31536000, X-FRAME-OPTIONS=SAMEORIGIN, SPRequestDuration=64, SPIisLatency=1, MicrosoftSharePointTeamServices=, X-Content-Type-Options=nosniff, X-MS-InvokeApp=1; RequireReadOnly, ... .
Out of these values, most of the headers are well-known – basic stuff. What’s piquing my interest is this one:
X-MSDAVEXT_Error=917656
That is a WebDAV (Web Distributed Authoring and Versioning) protocol returning an error for your request. While the error code isn’t (to my knowledge) officially documented anywhere, it’s commonly recognized to be a permissions-related issue. And obviously, the error text describes that as well.
This might be a symptom of a weird, internal authentication issue in SharePoint Online, caused by someone tripping on a wire in Microsoft’s nearest data center. Or it might actually come from Azure AD in the background. It’s either one of those two, or something else :)
What’s important, is how to fix it. And that’s described below!
Solution
Running a couple of magic PowerShell spells (or commandlets, if you wish) might start a weird, internal background process, that will eventually enable the login for your SharePoint Online credentials. To be fair, I don’t even know 100% what these 2 switches do. Below, I’m offering my best guesses, on why this works like this. Proceed with caution and at your risk.
Time needed: 12 hours
How to fix “The website does not support SharePoint Online credentials. The response status code is ‘Unauthorized'” or “MSDAVEXT_Error=917656”?
- Fire up your PowerShell console
If you have SharePoint Online Management Shell, feel free to use that. If not, just use PowerShell instead.
- Verify you’re using the latest module versions
Before doing anything more drastic, it’s worth verifying you have the latest versions of the necessary PowerShell modules available, as Maciej brings up in the comments section.
If you’re using an outdated version of PowerShell commandlets, it’s quite possible that a simple module update will resolve your issue. So, before flipping any of the more exotic PowerShell switches, run the commands below and see if they help:# Uninstall your current versions of SharePoint PnP Powershell Online and install the latest
Uninstall-Module SharePointPnPPowerShellOnline
Install-Module SharePointPnPPowerShellOnline
# Uninstall your current version of SharePoint Online Management module and install the latest
Uninstall-Module Microsoft.Online.SharePoint.PowerShell
Install-Module Microsoft.Online.SharePoint.PowerShell
Then try to log in again. If that didn’t help, proceed! - Flip ’em switches!
Next, run these commandlets (if you want to be careful, first-run Get-SPOTenant with switches to see the values before the changes – and check with the environment’s IT and/or security team if they are other than defaults):
Connect-SPOService
Set-SPOTenant -LegacyAuthProtocolsEnabled $True
Set-SPOTenant -RequireAcceptingAccountMatchInvitedAccount $False
(see below for documentation of the switches)
It’s a bit weird, but seems to do the trick! It might take a moment for the changes to be propagated to all systems – or, like I suspect, the background job that gets started by “updating” these values (even if you just save them with their default values) to do whatever it does.
On the two occasions that I have had to do it, it took overnight for the authentication to then start to work. I’ve heard from others, that for them it’s been updated in 30 minutes. The bottom line seems to be not to fret until some 12 hours after the change has been made.
What’s “Set-SPOTenant -LegacyAuthProtocolsEnabled” or “-RequireAcceptingAccountMatchInvitedAccount” supposed to do?
Admittedly, the documentation for these 2 switches hasn’t been that good. Below, you can see the documentation as it was in early 2018 – community contributors (myself included) have improved it since, though!
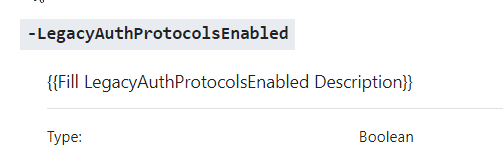
In short, Set-SPOTenant is used to set different properties on your tenant. These properties might be feature flags, authentication methods, integrations, or other configurations. Or, like in our case, fine-tuning how authentication works.
The following list offers possible explanations why these switches might help:
LegacyAuthProtocolsEnabled
- This is $True by default, (see “more info” for links to Microsoft’s documentation) since otherwise a lot of apps (probably all but those using Modern authentication flow) will fail in the authentication.
- Figure 1 shows Microsoft’s documentation for this switch before community contributions (such as mine) to the documentation.
- Note also this: “[Setting this to $False] may also prevent third-party apps from accessing SharePoint Online resources. Also, this will also block apps using the SharePointOnlineCredentials class to access SharePoint Online resources. For additional information about SharePointOnlineCredentials, see SharePointOnlineCredentials class.”
- If you can modify the code or script that causes this error, you can also migrate away from using legacy authentication – and use Managed Identities or Web Login (for example) instead! And if your customer requires this switch to be $False, the code changes are going to be your only way forward.
RequireAcceptingAccountMatchInvitedAccount
- This should be $False by default – but setting this property might, just like with the other one, cause some weird background service to start, and eventually fix the issue.
- Verify your current setting first by running Get-SPOTenant -RequireAcceptingAccountMatchInvitedAccount
- This is for external accounts, and shouldn’t matter if you have a *.onmicrosoft.com account, or even a federated domain account. It should work pretty much in any case.
- Microsoft’s explanation:
- Ensures that an external user can only accept an external sharing invitation with an account matching the invited email address.
- Administrators who desire increased control over external collaborators should consider enabling this feature.
- Note, that this only applies to new external users accepting new sharing invitations. Also, the resource owner must share with an organizational or Microsoft account, or the external user will be unable to access the resource.
The valid values are:
- False (default) – When a document is shared with an external user, bob@contoso.com, it can be accepted by any user with access to the invitation link in the original e-mail.
- True – The user must accept this invitation with bob@contoso.com.
Since running these commands will change the authentication behavior of the tenant, please don’t run them without running the changes by the customer’s IT. And most importantly, don’t say that I didn’t warn you!
Anyway, I hope it helps, even if you’re just setting the already existing values again. It did resolve the issue for us.
References
- Sources:
- https://technet.microsoft.com/en-in/library/fp161390.aspx
- https://blog.areflyen.no/2017/06/18/problem-with-connecting-to-sharepoint-online-in-office-365-with-powershell-sharepoint-designer-and-other-3-party-tools/
- https://docs.microsoft.com/en-us/powershell/module/sharepoint-online/set-spotenant?view=sharepoint-ps
- Another very similar issue I’ve posted about: