This article explains how to refresh the Visual Studio credentials on your development machine to keep your application using some sort of an authentication implementation relying on DefaultAzureCredential working.
Your app might be designed to be ran in an Azure app service, on AKS, on a dusty old server or from a scheduled task on Dave’s machine, but one thing is certain: you need some sort of authentication to access Azure resources, and being the smart cookie you are, you used DefaultAzureCredential to avoid having to write a lot of code to handle different environmets.
But if you’re like me, you also just expect the DefaultAzureCredential implementation to keep working… Any sometimes it doesn’t.
Background
DefaultAzureCredential is the best invention since sliced bread. It is yet another step towards being able to ignore where your code is running, and enables you to use multiple different authentication methods until one works.
Essentially, it allows you to do something like this:
KeyVaultClient = new SecretClient(new Uri($"https://{Configuration["KeyVaultName"]}.vault.azure.net/"), new DefaultAzureCredential());And on your development machine it’ll use the account you’ve used in Visual Studio (or Visual Studio code) to authenticate to Azure, in your test environment it’ll use EnvironmentCredential (reading the values from Environment Variables), in your production Kubernetes deployment it’ll use WorkloadIdentity and in whatever weird app service -based administration backend you might have (I’m not judging), it’ll grab the ManagedIdentity instead.
It’s elegant, convenient and pretty.
The magic is in the wide variety of credentials it tries to use: It will try the following credentials (in the order) and stops whenever it find ones that works:
- EnvironmentCredential
- WorkloadIdentityCredential
- ManagedIdentityCredential
- SharedTokenCacheCredential
- VisualStudioCredential
- VisualStudioCodeCredential
- AzureCliCredential
- AzurePowerShellCredential
- AzureDeveloperCliCredential
- InteractiveBrowserCredential
In theory, this means that as long as you have configured one of these, your implementation based on DefaultAzureCredential will “just work”.
But sometimes it’s a bit more complicated than that.
Problem
In my case, I definitely had one or more credentials Azure CLI credentials set up on my development machine – but I’m not sure how does my app know which one to use? I definitely also had multiple Azure PowerShell credentials lying in a cache somewhere – so in order to avoid the mess those might introduce, should my app go all the way down the stack to try and use them, I wanted to use a VisualStudioCredential instead.
And I did set one up, and it did work just fine for quite a while. Nice!
But I wouldn’t be writing an article with a title like this if the credential would just work by itself forever, would I?
Reason
Well, the credential DOES expire and needs to be refreshed every now and then.
And no, as things stand right now (November 2024, .NET 8, Visual Studio 17.3), Visual Studio doesn’t tell you that’s what needs to be done. It just silently fails the authentication with VisualStudioCredential and continues with other credential alternatives (it still has VisualStudioCodeCredential, AzureCliCredential, AzurePowerShellCredential, AzureDeveloperCliCredential and InteractiveBrowserCredential to try, after all).
Somehow, none of my credentials worked, though – my Azure Key Vault access just randomly started failing without any details.
Solution
Alright, let’s rule the obvious case out and make sure whatever credential DefaultAzureCredential is using is valid.
And the easiest way to be sure of that, is to make sure at least your VisualStudio credential is valid.
So let’s make sure there’s nothing fishy with that configuration, shall we?
1. Navigate to Azure Service Authentication settings
Open Tools > Options > Azure Service Authentication.
Check if the account in the “Choose an account” dropdown is the right one
In my case, this should be a “Microsoft account” (consumer account), but this will vary depending on your configuration.
If the account name looks correct, proceed to the next step.
Double-check if it complains about your credentials
Even if the selected account might be correct, it could still be expired (Visual Studio doesn’t automatically refresh it).
Clicking on “Re-enter your credentials” will, depending on multiple factors, either require you to reauthenticate or refresh the token in the cache for you.
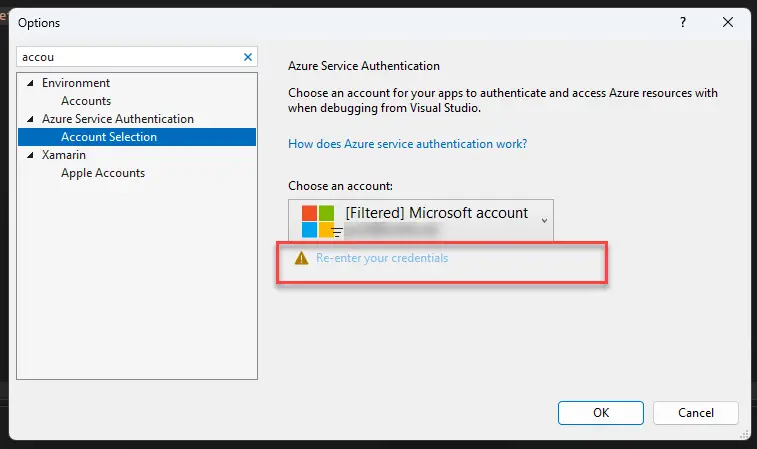
Either way, you should be good to go afterwards!
Rebuild and retry
Give it another go, and you should be good this time!
… if your issue was because of an expired Visual Studio credential, that is. If it wasn’t, have fun checking your Key Vault and other Azure configuration, I guess… 😅

